Time: 2025-02-21 11:03:08View:
Designing an FPGA-based Image and Video Encryption and Decryption System involves implementing cryptographic algorithms on an FPGA to secure image and video data. FPGAs are ideal for this task due to their parallel processing capabilities, low latency, and reconfigurability. Below is a detailed guide to designing such a system:
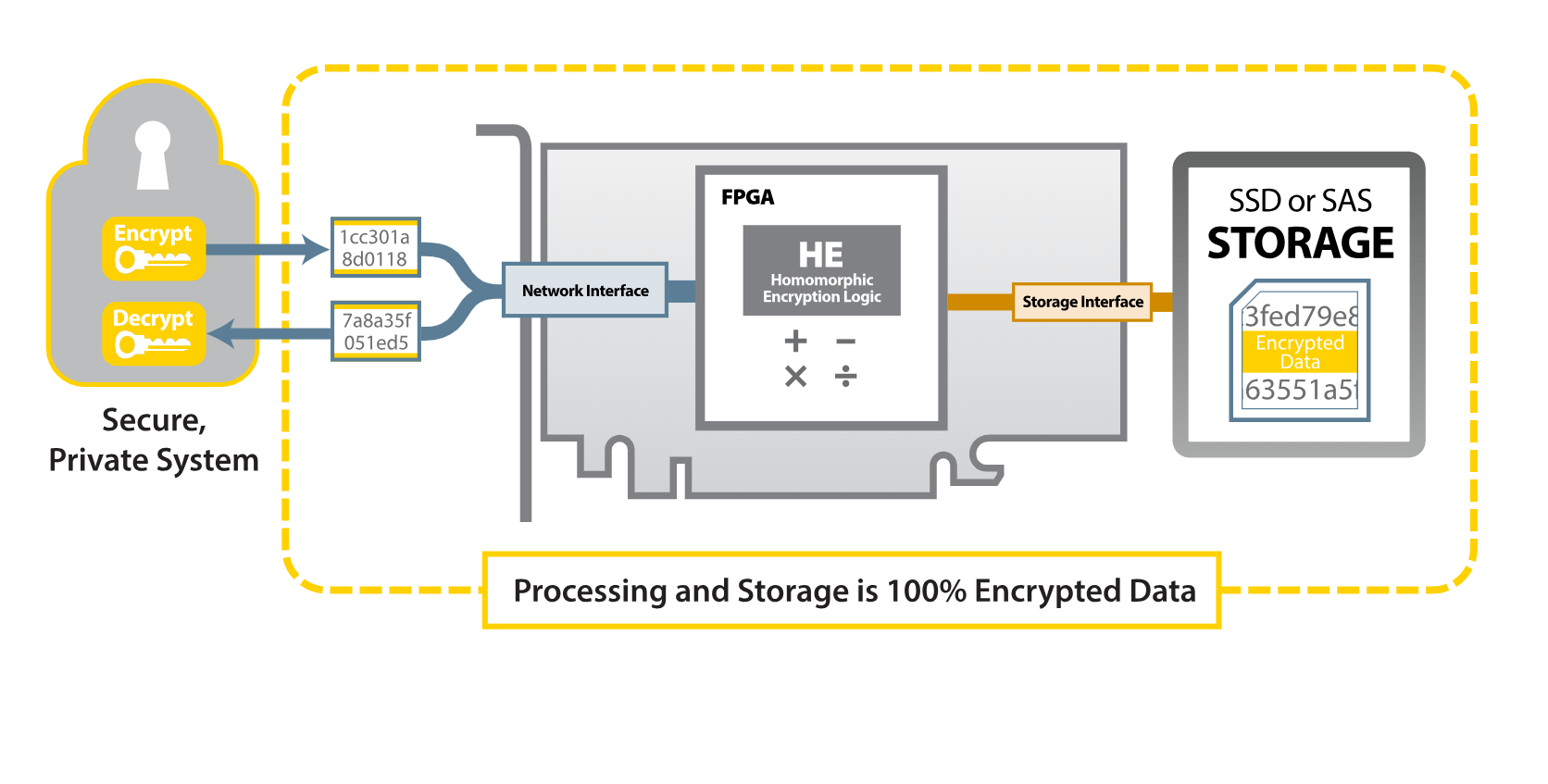
The system performs the following tasks:
Encryption: Secures image or video data using a cryptographic algorithm.
Decryption: Recovers the original data from the encrypted data.
Key Management: Handles encryption/decryption keys securely.
Common algorithms for image and video encryption include:
AES (Advanced Encryption Standard): Symmetric-key algorithm widely used for its security and efficiency.
DES (Data Encryption Standard): Older symmetric-key algorithm, less secure than AES.
RSA (Rivest-Shamir-Adleman): Asymmetric-key algorithm for key exchange.
Chaotic Maps: Used for lightweight and fast encryption in image processing.
For this design, we will focus on AES-128 due to its balance of security and performance.
FPGA: Core processing unit (e.g., Xilinx Zynq, Intel Cyclone, or Altera DE series).
Camera Module: For capturing video or image input.
Memory: DDR RAM or onboard Block RAM for storing image/video data.
Display Interface: HDMI, VGA, or LCD for output.
Communication Interface: UART, SPI, or I2C for external communication.
Capture image or video frames using a camera module.
Store the raw data in memory for processing.
Divide the image/video into blocks (e.g., 128-bit blocks for AES).
Encrypt each block using the AES algorithm.
Store or transmit the encrypted data.
Retrieve the encrypted data.
Decrypt each block using the AES algorithm with the same key.
Reconstruct the original image/video.
Securely store or exchange encryption/decryption keys.
Use a key expansion module to generate round keys for AES.
AES-128 operates on 128-bit blocks and uses a 128-bit key. It consists of the following steps:
Key Expansion: Generate round keys from the initial key.
Initial Round: AddRoundKey (XOR with the initial key).
Main Rounds (10 rounds for AES-128):
SubBytes (Substitution using S-Box)
ShiftRows (Row shifting)
MixColumns (Column mixing)
AddRoundKey (XOR with round key)
Final Round:
SubBytes
ShiftRows
AddRoundKey
Use Verilog or VHDL to describe the system:
Key Expansion Module: Generate round keys.
Encryption Module: Perform AES encryption on each block.
Decryption Module: Perform AES decryption on each block.
Memory Interface: Read/write image/video data from/to memory.
module aes_encryption ( input clk, input rst, input [127:0] plaintext, input [127:0] key, output reg [127:0] ciphertext); reg [127:0] state; reg [127:0] round_keys [0:10]; integer round; // Key Expansion (simplified for illustration) always @(posedge clk or posedge rst) begin if (rst) begin for (round = 0; round <= 10; round = round + 1) round_keys[round] <= 0; end else begin round_keys[0] <= key; // Generate round keys (key expansion logic) // ... end end // Encryption always @(posedge clk or posedge rst) begin if (rst) begin state <= 0; ciphertext <= 0; end else begin state <= plaintext ^ round_keys[0]; // Initial Round for (round = 1; round <= 10; round = round + 1) begin // SubBytes // ShiftRows // MixColumns (except final round) // AddRoundKey end ciphertext <= state; end endendmodule
Parallelism: Process multiple blocks simultaneously.
Pipelining: Break the AES rounds into stages for higher throughput.
Resource Sharing: Reuse hardware for encryption and decryption.
Fixed-Point Arithmetic: Use fixed-point representation for efficiency.
Simulate the design using tools like Xilinx Vivado or Intel Quartus.
Test with sample images/videos to verify encryption and decryption accuracy.
Measure performance metrics (e.g., latency, throughput).
Secure video conferencing
Digital rights management (DRM)
Military and surveillance systems
Medical imaging
Key Management: Securely store and exchange keys.
Real-Time Performance: Optimize for low latency and high throughput.
Resource Utilization: Balance performance and FPGA resource usage.
By leveraging the FPGA's parallel processing capabilities, this system can achieve high-speed, real-time encryption and decryption, making it suitable for applications requiring secure image and video processing.